A Beginner's Journey into Cryptography
Auther:Zahra Kasmouti is a cryptography-focused cybersecurity engineer.
She has a technical skillset in computer science and cybersecurity, complemented by a rigorous mathematical understanding. This combination allows her to not only understand cryptographic theory but also to effectively implement it into practical and secure applications.
Zahra Kasmouti LinkedinIntroduction
If you hear the word "cryptography," your mind might jump to cryptocurrencies, the padlock icon on your web browser, or secure messaging apps. While these are all modern applications, cryptography is a science with ancient roots, a fundamental pillar of the digital world that secures our daily lives.
At its core, cryptography is the science of securing communication against adversaries. Its historical goal was to hide the meaning of a message, but today it also ensures a message's integrity (that it wasn't altered) and authenticity (who it came from). This stands in contrast to cryptanalysis, the science of breaking cryptosystems. Together, they form the field of cryptology, a continuous battle between creating and cracking codes.
Cryptography is Everywhere
From the moment you wake up, you interact with cryptography. It's not just for spies or hackers; it's a ubiquitous part of modern technology:
- Communication: Secure Shell (SSH) for remote server access, VPNs Virtual Private Network, and encrypted email via plugins like S/MIME
- Finance: The chip in your bank card, the HTTPS connection for online banking.
- Personal Devices: Full-disk encryption on your laptop, encryption on your cell phone, and even your e-Passport or e-citizen card
- Entertainment: Your Kindle ebooks are protected by cryptographic systems
The Basic Setup: Alice, Bob, and Oscar
To understand cryptography, we use a classic scenario. Two parties, Alice and Bob, want to communicate over an insecure channel. The problem is an eavesdropper, Oscar, who can listen to everything they say.
The solution seems simple: Alice scrambles (encrypts) her message into unreadable ciphertext before sending it. Bob, who knows the secret, can unscramble (decrypt) it. Oscar, intercepting only the scrambled message, can't understand it.
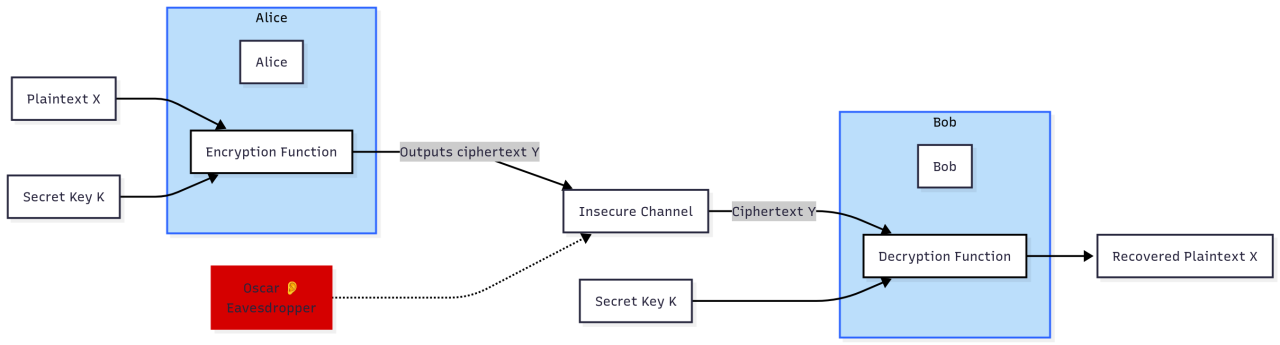
Figure 1 : Secure communication over insecure channel
A Revolutionary Principle: Kerckhoffs' Law
A seemingly stupid question arises: Should the encryption algorithm itself be secret?
Historically, from the encrypted hieroglyphs of ancient Egypt to the complex ciphers of medieval Europe, the answer was always "yes." However, this is a stupid approach. A secure cryptographic system is one that cannot be broken even when the algorithm is entirely public.
This counterintuitive idea was formalized in 1883 by Auguste Kerckhoffs. Kerckhoffs' Principle states that a cryptosystem should be secure even if everything about it is public knowledge, except for the secret key.
Why is this so important? Public scrutiny is the only way to prove strength. When algorithms are published, cryptanalysts worldwide try to break them. Those that withstand decades of attacks become the trusted standards we use today. This leads to a critical rule of thumb: Never roll your own crypto!! Always use standardized, publicly-examinated algorithms.
A Glimpse into History: The Substitution Cipher
Let's look at a simple, historical cipher to see these principles in action. The Substitution Cipher operates on letters by replacing every plaintext letter with a fixed ciphertext letter.
Example:
- A → L
- B → D
- C → W
- E → Q
So, the plaintext `ABBC` would encrypt to `LDDW`.
While this was used for centuries, it's highly vulnerable to two main types of cryptanalytic attacks:
1. Brute-Force Attack: The attacker (Oscar) tries every possible key. While there are about 26! ~ 2^88 possible substitution keys, modern computers can brute-force this easily.
2. Frequency Analysis: This is an analytical attack. In any language, some letters appear more often than others (e.g., 'E' is the most common letter in English). If 'E' is always encrypted as 'Q', then 'Q' will be the most frequent letter in the ciphertext. By analyzing these frequencies, Oscar can quickly crack the code without trying all keys.
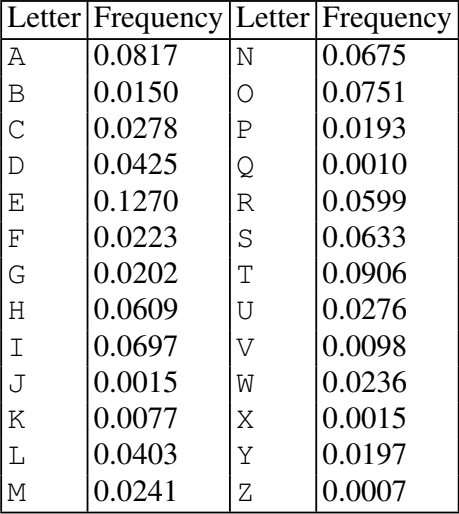
Figure 2 : Relative letter frequencies of the English language
Classifying Cryptographic Attacks
Cryptanalysis is not just about math. Attacks can come from many directions:
- Classical Cryptanalysis: Includes brute-force and analytical attacks (like frequency analysis) that target the algorithm's mathematical structure.
- Social Engineering: Bypassing the crypto entirely by tricking a person. "Hello, this is IT support. We need your password to fix a virus on your computer."
- Implementation Attacks: Attacking the physical system running the algorithm. For example, a side-channel attack might measure the power consumption of a smart card during decryption to deduce the secret key.
The Modern Cryptographic Toolkit
Today, cryptography is built on a set of powerful tools:
- Symmetric Algorithms: These use the same secret key for encryption and decryption (as in our Alice & Bob example). They are fast and are widely used for bulk data encryption. All cryptography until 1976 was symmetric.
- Asymmetric (Public-Key) Algorithms: Introduced by Diffie, Hellman, and Merkle, this was a revolution. Here, each user has a mathematically linked public key (shared with everyone) and a private key (kept secret). This enables applications like digital signatures and secure key exchange without a pre-shared secret.
- Cryptographic Protocols: These are the "recipes" that use cryptographic algorithms as ingredients to build complex security services. The Transport Layer Security (TLS) protocol, which creates the secure HTTPS connection for your online banking, is a prime example.
Conclusion
The journey of cryptography is one of constant evolution. From the secret hieroglyphs of ancient Egypt to the sophisticated cryptosystems securing our digital lives. By understanding its core principles, like Kerckhoffs' Law, and the different types of algorithms and attacks, we gain an appreciation for the invisible shield that protects our information every day. It is a fascinating discipline where security is proven not through secrecy, but through open challenge and resilience.
This work is derived from educational materials by Christof Paar, including his "Introduction to Cryptography" lecture and the overview of the foundational book "Understanding Cryptography" co-authored with Jan Pelzl and Tim Güneysu.
